ZIP: 227
Title: Issuance of Zcash Shielded Assets
Owners: Pablo Kogan <[email protected]>
Vivek Arte <[email protected]>
Daira-Emma Hopwood <[email protected]>
Jack Grigg <[email protected]>
Credits: Daniel Benarroch
Aurelien Nicolas
Deirdre Connolly
Teor
Status: Draft
Category: Consensus
Created: 2022-05-01
License: MIT
Discussions-To: <https://github.com/zcash/zips/issues/618>
Pull-Request: <https://github.com/zcash/zips/pull/680>
Terminology 
The key words "MUST", "MUST NOT", "SHOULD", "RECOMMENDED", and "MAY" in this document are to be interpreted as described in BCP 14 1 when, and only when, they appear in all capitals.
The term "network upgrade" in this document is to be interpreted as described in ZIP 200 7.
The character § is used when referring to sections of the Zcash Protocol Specification. 24
The terms "Orchard" and "Action" in this document are to be interpreted as described in ZIP 224 9.
We define the following additional terms:
- Asset: A type of note that can be transferred on the Zcash blockchain. Each Asset is identified by an Asset Identifier Specification: Asset Identifier, Asset Digest, and Asset Base.
- ZEC is the default (and currently the only defined) Asset for the Zcash mainnet.
- TAZ is the default (and currently the only defined) Asset for the Zcash testnet.
- We use the term "Custom Asset" to refer to any Asset other than ZEC and TAZ.
- Issuance Action: an instance of a single issuance of a Zcash Shielded Asset. It defines the issuance of a single Asset Identifier.
- Issuance Bundle: the bundle in the transaction that contains all the issuance actions of that transaction.
Abstract 
This ZIP (ZIP 227) proposes the Orchard Zcash Shielded Assets (OrchardZSA) protocol, in conjunction with ZIP 226 10. This protocol is an extension of the Orchard protocol that enables the creation, transfer and burn of Custom Assets on the Zcash chain. The creation of such Assets is defined in this ZIP (ZIP 227), while the transfer and burn of such Assets is defined in ZIP 226 10. This ZIP must only be implemented in conjunction with ZIP 226 10. The proposed issuance mechanism is only valid for the OrchardZSA transfer protocol, because it produces notes that can only be transferred via this protocol.
Motivation 
This ZIP introduces the issuance mechanism for Custom Assets on the Zcash chain. While originally part of a single ZSA ZIP, the issuance mechanism turned out to be substantial enough to stand on its own and justify the creation of this supporting ZIP for ZIP 226 10.
This ZIP only enables transparent issuance. As a first step, transparency will allow for proper testing of the applications that will be most used in the Zcash ecosystem, and will enable the supply of Assets to be tracked.
The issuance mechanism described in this ZIP is broad enough for issuers to either create Assets on Zcash (i.e. Assets that originate on the Zcash blockchain), as well as for institutions to create bridges from other chains and issue Assets that wrap tokens from those chains. This enables what we hope will be a useful set of applications.
Use Cases 
The design presented in this ZIP enables issuance of shielded Assets in various modes:
- The issuer may or may not know the receivers of the issued Asset in advance.
- The Asset can be of non-fungible type, where each Asset type can be made part of a single “series”.
- The supply of the Asset can be limited in advance or not.
- The Asset can be a wrapped version of an Asset issued by another chain (as long as there is a bridge that supports transfer of that Asset between chains).
See the Concrete Applications section for more details.
Requirements 
- Any user of the Zcash blockchain can issue Custom Assets on chain.
- The issuance mechanism should enable public tracking of the supply of the Assets on the Zcash blockchain.
- Issuing or changing the attributes of a specific Asset should require cryptographic authorization.
- The Asset identification should be unique (among all shielded pools) and different issuer public keys should not be able to generate the same Asset Identifier.
- An issuer should be able to issue different Assets in the same transaction. In other words, in a single "issuance bundle", the issuer should be able publish many "issuance actions", potentially creating multiple Custom Assets.
- Every "issuance action" should contain a \(\mathsf{finalize}\) boolean that defines whether the specific Custom Asset can have further tokens issued or not.
Specification: Asset Identifier, Asset Digest, and Asset Base 
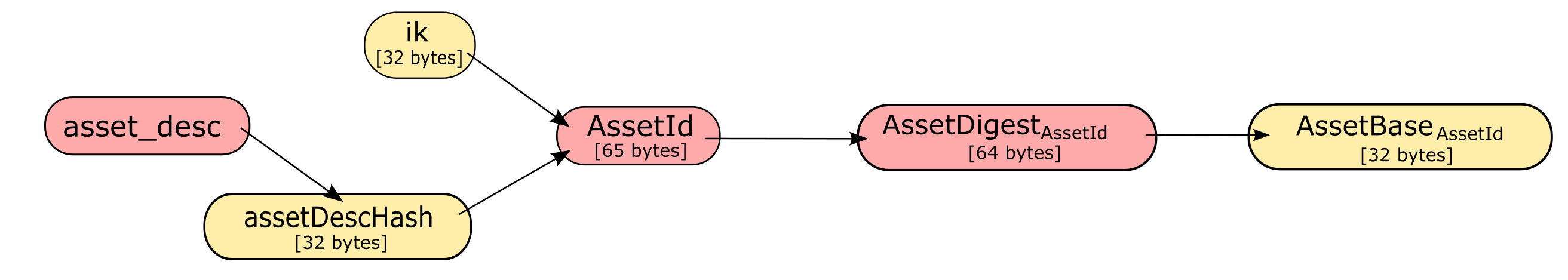
The definition of the Asset Identifier, and that of the Asset Digest and Asset Base for a given Asset Identifier, will be described in this section. For context, the relations between the Asset Identifier, Asset Digest, and Asset Base are shown in the following diagram:

Note: To keep notations light and concise, we may omit \(\mathsf{AssetId}\) in the subscript when the Asset Identifier is clear from the context.
Asset Identifier 
Every Asset has a globally-unique Asset Identifier, denoted \(\mathsf{AssetId}\!\) . A given Asset Identifier is used across all Zcash protocols that support ZSAs -- that is, the OrchardZSA protocol and potentially future Zcash shielded protocols.
ZIP 227 Asset Identifiers 
Assets issued using the protocol specified in this ZIP are scoped to the \(\mathsf{issuer}\) that issued them. Within that scope, Asset Identifier uniqueness is obtained by way of an asset description, \(\mathsf{asset\_desc}\!\) , which includes any information pertaining to the issuance. \(\mathsf{asset\_desc}\) is a non-empty byte sequence which SHOULD be a well-formed UTF-8 code unit sequence according to Unicode 15.0.0 or later.
Define
We define Asset Identifiers for Assets issued under this ZIP as
and define their canonical encoding as
Note that the initial \(\mathtt{0x00}\) byte is a version byte, enabling future ZIPs to specify alternative issuance protocols and Asset Identifiers. (This should not be confused with the first byte of \(\mathsf{issuer}\!\) , currently equal to the first byte of \(\mathsf{ik\_encoding}\!\) , that indicates the issuance signature scheme.)
Wallets MUST NOT display just the \(\mathsf{asset\_desc}\) string to their users as the name of the Asset. Some possible alternatives include:
- Wallets could allow clients to provide an additional configuration file that stores a one-to-one mapping of names to Asset Identifiers via a petname system 35. This allows clients to rename the Assets in a way they find useful. Default versions of this file with well-known Assets listed can be made available online as a starting point for clients.
- The Asset Digest could be used as a more compact byte sequence to uniquely determine an Asset, and wallets could support clients scanning QR codes to load Asset information into their wallets.
Asset Digests 
From the Asset Identifier, we derive an Asset Digest
where \(\mathsf{EncodeAssetId}(\mathsf{AssetId})\) is the canonical encoding scheme for the Asset Identifier.
Asset Bases 
From the Asset Digest, we derive a specific Asset Base that represents the Custom Asset within each shielded protocol:
This Asset Base is included in shielded notes within the shielded protocol.
OrchardZSA Asset Bases 
In the case of the OrchardZSA protocol, we define
where \(\mathsf{GroupHash}^\mathbb{P}\) is defined as in 32.
Specification: Issue Note, Issuance Action, Issuance Bundle and Issuance Protocol 
Issue Note 
Let \(\ell_{\mathsf{value}}\) be as defined in §5.3 ‘Constants’ 30. An Issue Note represents that a value \(\mathsf{v} : \{0 .. 2^{\ell_{\mathsf{value}}} - 1\}\) of a specific Custom Asset is issued to a recipient. An Issue Note is a tuple \((\mathsf{d}, \mathsf{pk_d}, \mathsf{v}, \mathsf{AssetBase}, \text{ρ}, \mathsf{rseed})\!\) , where:
- \(\mathsf{d}: \mathbb{B}^{[\ell_{\mathsf{d}}]}\) is the diversifier of the recipient's shielded payment address, as in §3.2 ‘Notes’ 26.
- \(\mathsf{pk_d}: \mathsf{KA}^{\mathsf{Orchard}}.\mathsf{Public}\) is the recipient's diversified transmission key, as in §3.2 ‘Notes’ 26.
- \(\mathsf{v} : \{0 .. 2^{\ell_{\mathsf{value}}} - 1\}\) is the value of the note in terms of the number of Asset tokens.
- \(\mathsf{AssetBase}: \mathbb{P}^*\) is the Asset Base corresponding to the ZSA being issued in the Issue Note.
- \(\text{ρ}: \mathbb{F}_{q_{\mathbb{P}}}\) is used to derive the nullifier of the note, and is computed as in Computation of ρ.
- \(\mathsf{rseed}: \mathbb{B}^{[\mathbb{Y}^{32}]}\) MUST be sampled uniformly at random by the issuer.
ZIP 230 16 defines, in IssueNoteDescription, field encodings which together with
\(\mathsf{issuer}\)
from the parent Issuance Bundle and
\(\mathsf{AssetDescHash}\)
from the parent Issuance Action, specify an Issue Note.
Let \(\mathsf{Note^{Issue}}\) be the type of an Issue Note, i.e.
The note commitments of Issue Notes are computed in the same manner as for OrchardZSA Notes. They will be added to the note commitment tree as any other shielded note when the transaction issuing the Asset is included on chain. This prevents future usage of the note from being linked to the issuance transaction, as the nullifier key is not known to the validators and chain observers.
Issuance Action 
An issuance action, IssueAction, is the instance of issuing a specific Custom Asset, and contains the following fields:
assetDescHash: the hash of the Asset description, as defined in the ZIP 227 Asset Identifiers section.vNotes: an array of Issue Notes containing the unencrypted output notes to the recipients of the Asset.flagsIssuance: a byte that stores the \(\mathsf{finalize}\) boolean that defines whether the issuance of that specific Custom Asset is finalized or not.
The \(\mathsf{finalize}\) boolean is set by the Issuer to signal that there will be no further issuance of the specific Custom Asset. As we will see in Specification: Consensus Rule Changes, transactions that attempt to issue further amounts of a Custom Asset that has previously been finalized will be rejected.
The complete encoding of these fields into an IssueAction is defined in ZIP 230 15.
Issuance Bundle 
An issuance bundle is the aggregate of all the issuance-related information. Specifically, contains all the issuance actions and the issuer signature on the transaction SIGHASH that validates the issuance itself. It contains the following fields:
issuer: the issuer identifier, that allows the validators to verify that the \(\mathsf{AssetId}\) is properly associated with the issuer.vIssueActions: an array of issuance actions, of typeIssueAction.issueAuthSig: the encoding of a signature of the transaction SIGHASH, signed by the issuance authorizing key, \(\mathsf{isk}\!\) , that validates the issuance.
The issuance bundle is added within the transaction format as a new bundle. The detailed encoding of the issuance bundle as a part of the V6 transaction format is defined in ZIP 230 17.
Computation of ρ 
We define a function \(\mathsf{DeriveIssuedRho} : \mathbb{F}_{q_{\mathbb{P}}} \times \{0 .. 2^{32} - 1\} \times \{0 .. 2^{32} - 1\} \to \mathbb{F}_{q_{\mathbb{P}}}\) for Issue Notes in the OrchardZSA Protocol as follows:
where \(\mathsf{ToBase}^{\mathsf{Orchard}}\) is defined in §4.2.3 ‘Orchard Key Components’ 28, and \(\mathsf{PRF}^{\mathsf{expand}}\) is defined in §5.4.2 ‘Pseudo Random Functions’ 31.
The \(\text{ρ}\) field of an Issue Note is computed as
where \(\mathsf{nf}_{0,0}\) is the nullifier for the input note in the first Action in the first Action Group of the OrchardZSA Bundle of the transaction, \(\mathsf{index_{Action}}\) is the zero-based index of the Issuance Action in the Issuance Bundle, and \(\mathsf{index_{Note}}\) is the zero-based index of the Issue Note in the Issuance Action.
NOTE: This implicitly requires that there always is an Action Group in the OrchardZSA bundle of the transaction. This is enforced by a consensus rule in the Specification: Consensus Rule Changes section.
Issuance Protocol 
The issuer program performs the following operations:
For all actions IssueAction:
- encode \(\mathsf{asset\_desc}\) as a UTF-8 byte string.
- compute \(\mathsf{assetDescHash}\)
- compute \(\mathsf{AssetDigest}\) from the issuer identifier \(\mathsf{issuer}\) and \(\mathsf{assetDescHash}\) as decribed in the Specification: Asset Identifier, Asset Digest, and Asset Base section.
- compute \(\mathsf{AssetBase}\) from \(\mathsf{AssetDigest}\) as decribed in the Specification: Asset Identifier, Asset Digest, and Asset Base section.
- set the \(\mathsf{finalize}\) boolean as desired (if more issuance actions are to be created for this \(\mathsf{AssetBase}\!\) , set \(\mathsf{finalize} = 0\!\) , otherwise set \(\mathsf{finalize} = 1\!\) ).
- for each recipient
\(i\!\)
:
- generate an Issue Note, \(\mathsf{note}_i = (\mathsf{d}_i, \mathsf{pk}_{\mathsf{d}_i}, \mathsf{v}_i, \mathsf{AssetBase}, \text{ρ}_i, \mathsf{rseed}_i)\!\) .
- encode the
\(\mathsf{note}_i\)
into the vector
vNotesof theIssueAction.
- encode the
IssueActioninto the vectorvIssueActionsof the bundle.
For the IssueBundle (see “ZSA Issuance Bundle Fields” in 17):
- encode the
vIssueActionsvector. - fill the
issuerLengthandissuerfields using \(\mathsf{issuer}\!\) . - sign the SIGHASH transaction hash with the issuance authorizing key, \(\mathsf{isk}\!\) , using the \(\mathsf{IssueAuthSig}\) signature scheme. The signature is then added to the issuance bundle.
Note: The note commitment is not included in the IssuanceAction itself. As explained below, it is computed later by the validators and added to the note commitment tree.
Specification: Reference Notes and Global Issuance State 
Reference Notes 
A reference note for a Custom Asset MUST be included by the issuer as the first Note in the Action of the Issuance Bundle where that Custom Asset is being issued for the first time.
A reference note for a Custom Asset is an Issue Note where the value
\(\mathsf{v}\)
is set to
\(0\!\)
, the Asset Base (
\(\mathsf{AssetBase}\!\)
) corresponds to that of the Custom Asset, and the recipient address
\((\mathsf{d}, \mathsf{pk}_{\mathsf{d}})\)
is set to the default diversified payment address (i.e. the diversified payment address with diversifier index
\(0\!\)
) derived from the all-zero Orchard spending key using the algorithm specified in §4.2.3 ‘Orchard Key Components’ 28. This corresponds to a 43-byte u8 array with the following entries:
[ 204, 54, 96, 25, 89, 33, 59, 107, 12, 219, 150, 167, 92, 23, 195, 166, 104, 169, 127, 13, 106, 140, 92, 225, 100, 165, 24, 234, 155, 169, 165, 14, 167, 81, 145, 253, 134, 27, 15, 241, 14, 98, 176, ]
Global Issuance State 
The maximum total supply of any issued Custom Asset is denoted by the constant \(\mathsf{MAX\_ISSUE} := 2^{64} - 1\!\) .
Issuance requires the following additions to the global state:
A map, \(\mathsf{issued\_assets} : \mathbb{P}^* \to \{0 .. \mathsf{MAX\_ISSUE}\} \times \mathbb{B} \times \mathsf{Note^{Issue}}\!\) , from the Asset Base, \(\mathsf{AssetBase} : \mathbb{P}^*\!\) , to a tuple \((\mathsf{balance}, \mathsf{final}, \mathsf{note_{ref}})\!\) , for every Asset that has been issued. We use the notation \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{balance}\!\) , \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{final}\!\) , and \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{note_{ref}}\) to access, respectively, the elements of the tuple stored in the global state for a given \(\mathsf{AssetBase}\!\) . If \(\mathsf{issued\_assets}(\mathsf{AssetBase}) = \bot\!\) , it is assumed that \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{balance} = 0\!\) , \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{final} = 0\!\) , and \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{note_{ref}} = \bot\!\) .
For any Asset represented by \(\mathsf{AssetBase}\!\) :
- \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{balance} \in \{0 .. \mathsf{MAX\_ISSUE}\}\) stores the amount of the Asset in circulation, computed as the amount of the Asset that has been issued less the amount of the Asset that has been burnt.
- \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{final} : \mathbb{B}\) is a Boolean that stores the finalization status of the Asset (i.e.: whether the \(\mathsf{finalize}\) flag has been set to \(1\) in any preceding issuance transaction for the Asset). The value of \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{final}\) for any \(\mathsf{AssetBase}\) cannot be changed from \(1\) to \(0\!\) .
- \(\mathsf{issued\_assets}(\mathsf{AssetBase}).\mathsf{note_{ref}} : \mathsf{Note^{Issue}}\) stores the reference note for the Asset, as defined in the Reference Notes section.
Management of the Global Issuance State 
The issuance state, that is, the \(\mathsf{issued\_assets}\) map, MUST be updated by a node during the processing of any transaction that contains burn information, or an issuance bundle. The issuance state is chained as follows:
- The input issuance state for the activation block of the OrchardZSA protocol is the empty map.
- The input issuance state for the first transaction of a block is the final issuance state of the immediately preceding block.
- The input issuance state of each subsequent transaction in the block is the output issuance state of the immediately preceding transaction.
- The final issuance state of a block is the output issuance state of the last transaction in the block.
We describe the consensus rule changes that govern the management of the global issuance state in the Specification: Consensus Rule Changes section. We use \(\mathsf{issued\_assets}_{\mathsf{IN}}\) and \(\mathsf{issued\_assets}_{\mathsf{OUT}}\) to denote the input issuance state and output issuance state for a transaction, respectively.
Specification: Consensus Rule Changes 
Let \(\mathsf{SigHash}\) be the SIGHASH transaction hash of this transaction, as defined in §4.10 ‘SIGHASH Transaction Hashing’ 29 with the modifications described in ZIP 226 13, using \(\mathsf{SIGHASH\_ALL}\!\) .
For every transaction:
- The
nActionGroupsOrchardfield MUST have a value of either0or1and thenAGExpiryHeightfield MUST have a value of0. - The output issuance state of the transaction MUST be initialized to be the same as the input issuance state, \(\mathsf{issued\_assets}_{\mathsf{OUT}} = \mathsf{issued\_assets}_{\mathsf{IN}}\!\) .
- The \(\mathsf{assetBurn}\) set MUST satisfy the consensus rules specified in ZIP 226 12.
- It MUST be the case that for all \((\mathsf{AssetBase}, \mathsf{v}) \in \mathsf{assetBurn}\!\) , \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{balance} \geq \mathsf{v}\!\) . The node then MUST update \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase})\) prior to processing the issuance bundle in the following manner. For every \((\mathsf{AssetBase}, \mathsf{v}) \in \mathsf{AssetBurn}\!\) , \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{balance} = \mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{balance} - \mathsf{v}\!\) .
If the transaction contains an issuance bundle:
- It MUST also contain at least one OrchardZSA Action Group.
- The encoding
\(\mathsf{ik\_encoding}\)
of the issuance key
\(\mathsf{ik}\)
used to validate the issuance authorization signature MUST be taken from the
issuerfield, and MUST start with the byte value \(\mathtt{0x00}\) indicating a BIP 340 public key. - The issuance authorization signature, \(\mathsf{issueAuthSig}\!\) , MUST be a valid \(\mathsf{IssueAuthSig}\) signature over \(\mathsf{SigHash}\!\) , i.e. \(\mathsf{IssueAuthSig}.\!\mathsf{Validate}(\mathsf{ik}, \mathsf{SigHash}, \mathsf{issueAuthSig}) = 1\!\) .
- For every issuance action description (
\(\mathsf{IssueAction}_\mathsf{i},\ 1 \leq i \leq \mathtt{nIssueActions}\!\)
) in the issuance bundle:
- Every
IssueNoteDescriptionin theIssueActionMUST be a valid field encoding as defined in ZIP 230 16. - Let an Issue Note (with type
\(\mathsf{Note^{Issue}}\!\)
) be constructed from the fields of each
IssueNoteDescription, with the \(\mathsf{AssetBase}\) derived from theassetDescHashfield of theIssueActionand theissuerfield of the issuance bundle, as described in the Specification: Asset Identifier, Asset Digest, and Asset Base section. - It MUST be the case that \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{final} \neq 1\!\) .
- If
\(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{note_{ref}} = \bot\!\)
, then let
\(\mathsf{new\_note_{ref}}\)
be the first Issue Note in the Issuance Action.
- The recipient address \((\mathsf{d}, \mathsf{pk}_{\mathsf{d}})\) of \(\mathsf{new\_note_{ref}}\) MUST be the default diversified payment address derived from the all-zero Orchard spending key, as described in the Reference Notes section.
- The value of \(\mathsf{new\_note_{ref}}\) MUST be \(0\!\) .
- The node MUST update \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{note_{ref}} = \mathsf{new\_note_{ref}}\!\) .
- For every Issue Note,
\(\mathsf{note}_j\)
for
\(1 \leq j \leq \mathtt{nNotes}\)
in
IssueAction:- The \(\text{ρ}\) field of the issue note MUST have been computed as described in the Computation of ρ section.
- It MUST be the case that \(\mathsf{issued\_assets}_{\mathsf{OUT}}.\mathsf{balance} + \mathsf{v}_j \leq \mathsf{MAX\_ISSUE}\!\) , where \(\mathsf{v}_j\) is the value of \(\mathsf{note}_j\!\) . The node then MUST update \(\mathsf{issued\_assets}_{\mathsf{OUT}}.\mathsf{balance} = \mathsf{issued\_assets}_{\mathsf{OUT}}.\mathsf{balance} + \mathsf{v}_j\!\) .
- The node MUST compute the note commitment, \(\mathsf{cm}_{\mathsf{i,j}}\!\) , as defined in the Note Structure and Commitment section of ZIP 226 11.
- If
\(\mathsf{finalize} = 1\)
within the
flagsIssuancefield ofIssueAction, the node MUST set \(\mathsf{issued\_assets}_{\mathsf{OUT}}(\mathsf{AssetBase}).\mathsf{final} = 1\!\) .
- Every
Addition to the Note Commitment Tree 
If the transaction is added to the block chain, the note commitments of all the OrchardZSA Notes and the Issue Notes in the transaction are added to the note commitment tree of the associated treestate. The order of addition to the tree is as specified below:
- For each Action Group in the OrchardZSA Bundle:
- For every Action in the Action Group, append the note commitment of every new OrchardZSA note in the Action to the note commitment tree.
- For each Issue Action in the Issue Bundle:
- For every Issue Note in the Issue Action, append the note commitment of the Issue Note to the note commitment tree.
Rationale 
The following is a list of rationale for different decisions made in the proposal:
- The issuance key structure is independent of the original key tree, but derived in an analogous manner (via ZIP 32). This keeps the issuance details and the Asset Identifiers consistent across multiple shielded pools. It also separates the issuance authority from the spend authority, allowing for the potential transfer of issuance authority without compromising the spend authority.
- The Custom Asset is described via a combination of the issuer identifier and an asset description string, to preclude the possibility of two different issuers creating colliding Custom Assets.
- The requirement of at least one OrchardZSA Action Group in the presence of an issue bundle is both to allow for the computation of the \(\text{ρ}\) field of the issue notes, as well as to prevent replay attacks. If a transaction includes only an issue bundle, the SIGHASH transaction hash would be computed solely based on the issue bundle. A duplicate bundle would have the same SIGHASH transaction hash, potentially allowing for a replay attack.
Hash of the asset description 
In an earlier version of this ZIP, the asset description was a direct component of the Asset Identifier, and was stored on-chain in each issuance transaction. The Asset Identifier and issuance transactions now instead include a collision-resistant hash of the asset description, for the following reasons:
- A hash output (32 bytes per Issue Action) incurs lower average bandwidth costs in issuance transactions than the asset description (previously up to 512 bytes).
- The asset description can be longer than 512 bytes without incurring chain costs.
- Including an asset description byte string directly in issuance transactions does not ensure that the "user-visible" asset description is consensus-visible, because the byte string could itself be a hash of another off-chain description (even if the consensus rules had required it to be a Unicode string instead of only recommending it).
- The lack of key rotation in this issuance protocol means that it is not sufficient to mark an \(\mathsf{issuer}\) as trusted and then accept whatever asset descriptions are issued by it. Each Asset Identifier needs to be independently verified, which requires some out-of-band protocol that can also convey the corresponding asset description.
- If issuance transactions include the asset descriptions directly, wallets will discover them during scanning. This is an "attractive nuisance" because it would result in wallets being more likely to expose the asset description directly to users without any verification that the received asset has the value that a user might expect from that description. By instead using a collision-resistant hash of an asset description, wallets are forced to look up the corresponding asset description when a payment is received in an unknown asset. That lookup can be mediated by a trusted party or common trusted registry of known assets, or else will need to be approved directly by a user who can personally assert their interest in that specific asset.
Rationale for Global Issuance State 
It is necessary to ensure that the balance of any issued Custom Asset never becomes negative within a shielded pool, along the lines of ZIP 209 8. However, unlike for the shielded ZEC pools, there is no individual transaction field that directly corresponds to both the issued and burnt amounts for a given Asset. Therefore, we require that all nodes maintain a record of the current amount in circulation for every issued Custom Asset, and update this record based on the issuance and burn transactions processed. This allows for efficient detection of balance violations for any Asset, in which case we specify a consensus rule to reject the transaction or block.
We limit the total issuance of any Asset to a maximum of \(\mathsf{MAX\_ISSUE}\!\) . This is a practical limit that also allows an issuer to issue the complete supply of an Asset in a single transaction.
Nodes also need to reject transactions that issue Custom Assets that have been previously finalized. The \(\mathsf{issued\_assets}\) map allows nodes to store whether or not a given Asset has been finalized.
Concrete Applications 
Asset Features
- By using the
\(\mathsf{finalize}\)
boolean and the burning mechanism defined in 10, issuers can control the supply production of any Asset associated to their issuer keys. For example,
- by setting \(\mathsf{finalize} = 1\) from the first issuance action for that Asset Identifier, the issuer is in essence creating a one-time issuance transaction. This is useful when the max supply is capped from the beginning and the distribution is known in advance. All tokens are issued at once and distributed as needed.
- Issuers can also stop the existing supply production of any Asset associated to their issuer keys. This could be done by
- issuing a last set of tokens of that specific \(\mathsf{AssetId}\!\) , for which \(\mathsf{finalize} = 1\!\) , or by
- issuing a transaction with a single note in the issuance action pertaining to that \(\mathsf{AssetId}\!\) , where the note will contain a \(\mathsf{value} = 0\!\) . This can be used for application-specific purposes (NFT collections) or for security purposes to revoke the Asset issuance (see Security and Privacy Considerations).
- The issuance and burn mechanisms can be used in conjunction to determine the supply of Assets on the Zcash ecosystem. This allows for the bridging of Assets defined on other chains.
- Furthermore, NFT issuance is enabled by issuing in a single bundle several issuance actions, where each \(\mathsf{AssetId}\) corresponds to \(\mathsf{value} = 1\) at the fundamental unit level. Issuers and users should make sure that \(\mathsf{finalize} = 1\) for each of the actions in this scenario.
Modifications relative to ZIP 244 18
Relative to the sighash algorithm defined in ZIP 244, the sighash algorithm that applies to v6 transactions differs by including the issuance bundle components within the tree hash. See ZIP 246 19 for details.
Changes to ZIP 317 20
The conventional fee in ZEC is altered to take into account both the presence of issuance actions within a transaction, and the creation of new Custom Assets within the global chain state. See the Fee calculation section of ZIP 317 21 for details.
Rationale for paying fees in ZEC 
Click to show/hide
We choose to maintain the native ZEC Asset as the primary token for the Zcash blockchain, similar to how ETH is needed for ERC20 transactions to the benefit of the Ethereum ecosystem.
An alternative proposal for the OrchardZSA fee mechanism that was not adopted was to adopt a new type of fee, denominated in the custom Asset being issued or transferred. In the context of transparent transactions, such a fee allows miners to “tap into” the ZSA value of the transactions, rather than the ZEC value of transactions. However when transactions are shielded, any design that lifts value from the transaction would also leak information about it.
Security and Privacy Considerations 
Displaying Asset Identifier information to users 
Wallets need to communicate the names of the Assets in a non-confusing way to users, since the byte representation of the Asset Identifier would be hard to read for an end user. Possible solutions are provided in the Specification: Asset Identifier, Asset Digest, and Asset Base section.
Issuance Key Compromise 
The design of this protocol does not currently allow for rotation of the issuance validating key that would allow for replacing the key of a specific Asset. In case of compromise, the following actions are recommended:
- If an issuer identifier is compromised, the \(\mathsf{finalize}\) boolean for all the Assets issued with that key should be set to \(1\!\) ; then the issuer should change to a new issuance authorizing key (hence a new issuer identifier), and issue new Assets, each with a new \(\mathsf{AssetId}\!\) .
Bridging Assets 
For bridging purposes, the secure method of off-boarding Assets is to burn an Asset with the burning mechanism in ZIP 226 10. Users should be aware of issuers that demand the Assets be sent to a specific address on the Zcash chain to be redeemed elsewhere, as this may not reflect the real reserve value of the specific Asset.
Other Considerations 
Implementing Zcash Nodes 
Although not enforced in the global state, it is RECOMMENDED that Zcash full validators keep track of the total supply of Assets as a mutable mapping \(\mathsf{issuanceSupplyInfoMap}\) from \(\mathsf{AssetId}\) to \((\mathsf{totalSupply}, \mathsf{finalize})\) in order to properly keep track of the total supply for different Asset Identifiers. This is useful for wallets and other applications that need to keep track of the total supply of Assets.
Test Vectors 
- LINK TBD
Reference Implementation 
- LINK TBD
- LINK TBD
Deployment 
TBD
References 
| 1 | Information on BCP 14 — "RFC 2119: Key words for use in RFCs to Indicate Requirement Levels" and "RFC 8174: Ambiguity of Uppercase vs Lowercase in RFC 2119 Key Words" |
|---|
| 2 | ZIP 32: Shielded Hierarchical Deterministic Wallets |
|---|
| 3 | ZIP 32: Shielded Hierarchical Deterministic Wallets — Specification: Hardened-only key derivation |
|---|
| 4 | ZIP 32: Shielded Hierarchical Deterministic Wallets — Hardened-only child key derivation |
|---|
| 5 | ZIP 32: Shielded Hierarchical Deterministic Wallets — Key path levels |
|---|
| 6 | ZIP 32: Shielded Hierarchical Deterministic Wallets — Orchard key path |
|---|
| 7 | ZIP 200: Network Upgrade Mechanism |
|---|
| 8 | ZIP 209: Prohibit Negative Shielded Chain Value Pool Balances |
|---|
| 9 | ZIP 224: Orchard |
|---|
| 10 | ZIP 226: Transfer and Burn of Zcash Shielded Assets |
|---|
| 11 | ZIP 226: Transfer and Burn of Zcash Shielded Assets — Note Structure and Commitment |
|---|
| 12 | ZIP 226: Transfer and Burn of Zcash Shielded Assets — Additional Consensus Rules for the assetBurn set |
|---|
| 13 | ZIP 226: Transfer and Burn of Zcash Shielded Assets — TxId Digest |
|---|
| 14 | ZIP 226: Transfer and Burn of Zcash Shielded Assets — Authorizing Data Commitment |
|---|
| 15 | ZIP 230: Version 6 Transaction Format — Issuance Action Description (IssueAction) |
|---|
| 16 | ZIP 230: Version 6 Transaction Format — Issue Note Description (IssueNoteDescription) |
|---|
| 17 | ZIP 230: Version 6 Transaction Format — Transaction Format |
|---|
| 18 | ZIP 244: Transaction Identifier Non-Malleability |
|---|
| 19 | ZIP 246: Digests for the Version 6 Transaction Format |
|---|
| 20 | ZIP 317: Proportional Transfer Fee Mechanism |
|---|
| 21 | ZIP 317: Proportional Transfer Fee Mechanism — Fee calculation |
|---|
| 22 | BIP 43: Purpose Field for Deterministic Wallets |
|---|
| 23 | BIP 340: Schnorr Signatures for secp256k1 |
|---|
| 24 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1] or later. |
|---|
| 25 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 2: Notation |
|---|
| 26 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 3.2: Notes |
|---|
| 27 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 4.1.7: Signature |
|---|
| 28 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 4.2.3: Orchard Key Components |
|---|
| 29 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 4.10: SIGHASH Transaction Hashing |
|---|
| 30 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 5.3: Constants |
|---|
| 31 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 5.4.2: Pseudo Random Functions |
|---|
| 32 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 5.4.9.8: Group Hash into Pallas and Vesta |
|---|
| 33 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 5.6.4.2: Orchard Raw Payment Addresses |
|---|
| 34 | Zcash Protocol Specification, Version 2025.6.2 [NU6.1]. Section 7.1: Transaction Encoding and Consensus |
|---|
| 35 | An Introduction to Petname Systems. Marc Stiegler, updated June 2010. |
|---|